Email Viruses - tips on how to avoid
Receiving a malicious email with a virus attached (or a link that leads to a virus) is one of the most common ways of getting infected. Unfortunately spammers/malicious senders are getting smarter and emails can often look genuine.
Ensure you know how to avoid such emails by reading the tips below.
Beware of all emails - whether the sender is unknown or known
Impersonation - malicious senders will often adopt impersonation as an approach to lure you into clicking an attachment or link (phishing as its otherwise known). So even if the email appears like it's from your bank, post office, PayPal, or <insert utility company here>, then be wary until you know otherwise. Use the approaches outlined below to try and determine, or just avoid if in doubt. Well known companies/organisations generally don't send attachments, but they may send links.
Sometimes the email may come from a friend's legitimate email address. Free online email account services such as Hotmail are prone to brute force hacking, especially if your friend doesn't have a strong password. Once hackers infiltrate the email account it's common for the email address book or email addresses from previously received items to be collected and mass mailed with you know what! This is also a reason why your seemingly private email address ends up on spam lists, but that's an article for another day... Again proceed with caution.
Assessing emails
Links
Ok you've received an email you are unsure about and it contains links.
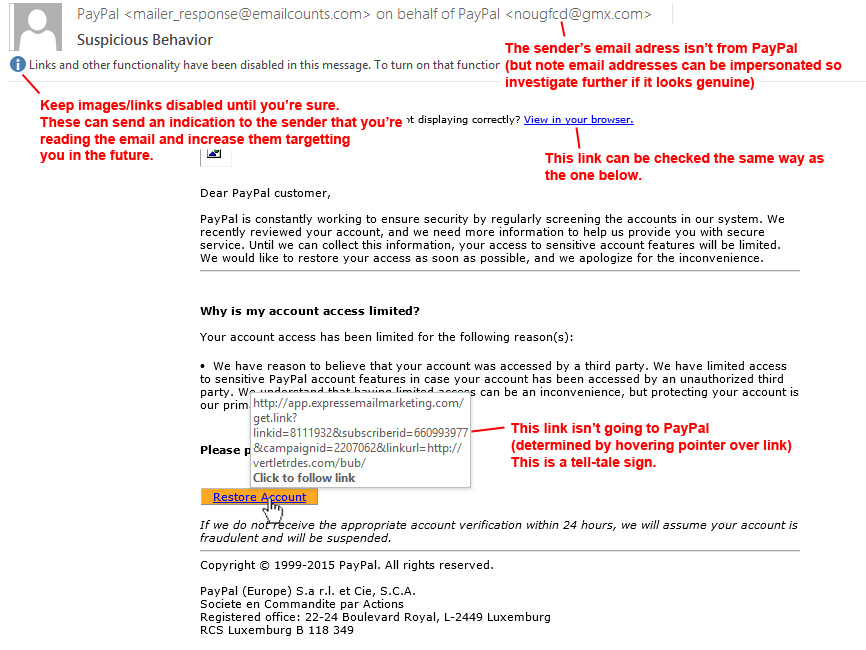
Links can display differently from the actual link behind them, take this link for example - http://www.google.co.uk (it actually goes to Yahoo). By hovering your mouse over the link in Outlook (or an email client), the real destination should reveal itself as a tool tip or in the status bar at the bottom. You can use this to verify if it's genuine, but better still if it's from a seemingly known recipient then go to the website the way you normally would by manually typing the address in the browsers address bar, following a bookmark, or using search engine etc (anything but the link!) to verify if what the email says is correct.
Below shows an example of how to determine if an email if genuine or not.
Attachments
You've received an email you are unsure of that contains an attachment.
Be wary here. All sorts of files can contain viruses, such as Word documents, Excel spreadsheets, and even Adobe PDF files. So if the sender is unknown, dismiss instantly.
If the attachment ends with .EXE, .COM or .BAT file (executable) then dismiss it instantly as these files can execute malicious code immediately. How do I know if it is this type? In Windows Explorer it's generally best to enable file extensions to be shown (see this guide from Microsoft). Some executable files may disguise themselves with known icons such as Adobe PDF, so showing extensions let's you know a bit more about what your dealing with.
Malicious files may also be within a ZIP file (see this BBC link for details on what ZIP files are).
Anti-Virus Protection
Ensure you have anti-virus and anti-malware (if the first doesn't cover malware) software installed to help prevent and remove viruses and other nuisance software. Note however virus protection is a cat and mouse game with anti-virus companies always play catch up. New variations of viruses can emerge that may not yet be not protected against, so even if you're anti-virus software doesn't detect it then that's no indication it isn't a virus!
Outlook - most anti-virus applications will install an add in in Outlook to help identify emails with viruses as they come in, but Outlook may automatically disable these add ins because they make it run slow! See this guide for always enabling add ins to ensure this doesn't happen.
Containment
Ok so you've accidentally clicked an attachment or link and something has run.
The first things to do are shut down your computer (power it off from the wall if it won't shut down) and disconnect it instantly from the network by pulling out the network lead to prevent it spreading onto the network. To clear the virus boot CDs are preferable because they will find it before the operating starts. But note you may have a yet undiscovered virus.
Some viruses are tame, others are nasty and can quickly do damage to your files and files on the network. One such virus is CryptoLocker which is ransomware and quickly begins to encrypt every file it can find on the network, then asks you to pay money to receive an unlock code.
If in doubt switch the computer off and contact your local IT support contact immediately. Always ensure you have a backup in place to recover important files that may get wiped.

